
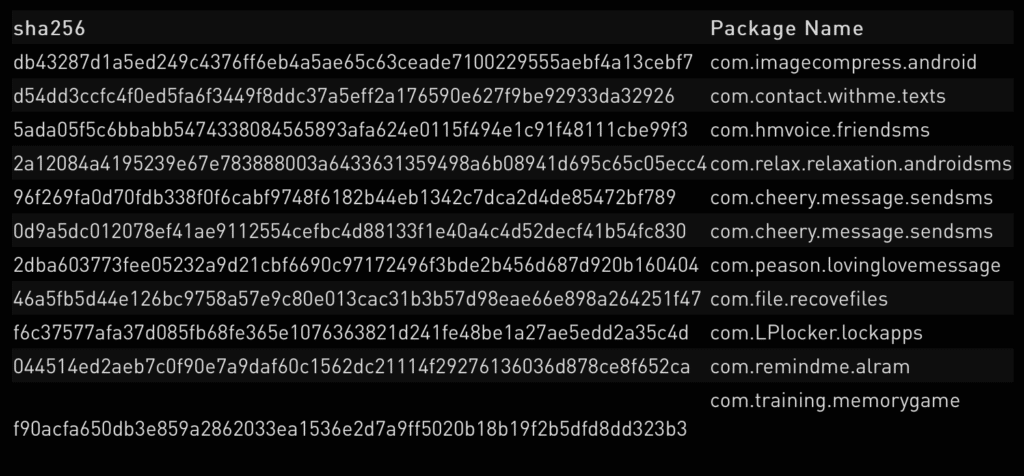
Recently google removed 11 malicious android applications from its official app marketplace due to a new variant of joker malware into them.
About Joker-Malware
All the malicious apps spreading the Joker malware have continued since 2019 because malware’s creator has kept on modifying the codes of the malware and kept on injecting it into a different number of apps. Researchers over the new variant of joker malware said that this time joker malware author is creating a major bar, and using a tactic that is hiding the malware so perfectly into legitimate apps making it completely undetectable in the Google Play’s app vetting process.
The malware first emerged in 2017 but after that, it suddenly appeared with its new and stronger variant in 2019. It tells itself as a legitimate app, but once installed into a victim’s mobile, what it actually does is, it steals the device info, SMS messages, like OTP and buys the premium service subscriptions and drains the victim’s money/wallet.
What researches have to say
Aviran Hazum, manager of Mobile Research said “Joker adapted,” in a Thursday analysis. “The Joker malware is tricky to detect, despite Google’s investment in adding Play Store protections. Although Google removed the malicious apps from the Play Store, we can fully expect Joker to adapt again. Everyone should take the time to understand what Joker is and how it hurts everyday people.”
The current scenarios related to malware
The recent variant of the malware uses a tactic in which it hides its malicious code inside the “Android Manifest” file of a legitimate app. Every application has an android manifesto inside which it has information related to the application such as name, about, icon and permissions to the android system.
But the author modified it in such a way that, he built the payload before inserting it into the android manifest file through dex file which is hidden in the form of Base64 encoded strings. Moreover, the payload is hidden during Google Play’s evaluation test of the app, making it easier for the malware to skirt by the app vetting process.
Researchers said that “It’s not until after the app has been approved in the evaluation process that the campaign starts to operate, with the malicious payload decoded and loaded onto the compromised device. It’s important to note that this trick is well-known to developers of malware for Windows PCs,”
“This way, the malware does not need to access a [command-and-control] server, which is a computer-controlled by a cybercriminal used to send commands to systems compromised by malware, to download the payload, the portion of the malware which performs the malicious action,” said researchers.
Researches also detected an “in-between” variant, that utilized the technique of hiding the .dex file as Base64 strings in-app. However, they also said “instead of adding the strings to the Manifest file, the strings were located inside an internal class of the main application,” said researchers. “In this case, all that was needed for the malicious code to run was to read the strings, decode them from Base64, and load it with reflection.”
in the form of encrypted strings
In January google had also removed 17,000 such apps with joker malware embedded into it , from the play store. At the time, researchers said that Joker’s operators have “at some point used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected.” In 2019, it was found that total 24 apps with such payloads had a total number of 472,000 downloads on the official app marketplace that is google play store.
“Our latest findings indicate that Google Play Store protections are not enough. We were able to detect numerous cases of Joker uploads on a weekly basis to Google Play, all of which were downloaded by unsuspecting users,” said Check Point researchers.
Get the latest tech news and updates, ethical hacking tutorials and cyber security tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.




Comments: