These are the writeups for Reverse Engineering Challenges of the Cohesion CTF by IEEE NCU.
1. Post Office

Opening the website gives us the following screen.

It says that we need to go to counter 22. If we click on Counter 1 button, it sends us over here.

Now, you can either keep clicking links and go to Counter 22 manually, or you can just edit the GET parameter to reach there more efficiently.
On the counter 22, we see a new button “Read The Letter”

When we click on this, we are sent to this page.

And then again to the counters. At the bottom of the page, it says that this is a POST office. Let’s try sending a POST request for the flag instead of GET request.

Go back to Counter 22 and inspect element of the page.

Now change GET over here to POST and clock the button now.

Voila, here’s the flag: cohesion.ctf{Y0u_h4v3_G0T_m41l}

2. Johnny With Tori

Opening up the website gives us the following screen.

There’s nothing here, except the animation, not even in the source code. Let’s try opening robots.txt

Disallow /flag/, that looks interesting. And on scrolling down, we also find a key over here. That might be useful later.

Anyways, let’s open the flag directory.

There’s a flag here, checking its value in the source code gives us a base64 encoded string. Decoding it gives us n0t_tH3_c0rr3ct-Fl4g
Which is obviously not the correct flag, guess its a rabbit hole then. Let’s intercept this request in burpsuit and see the request.
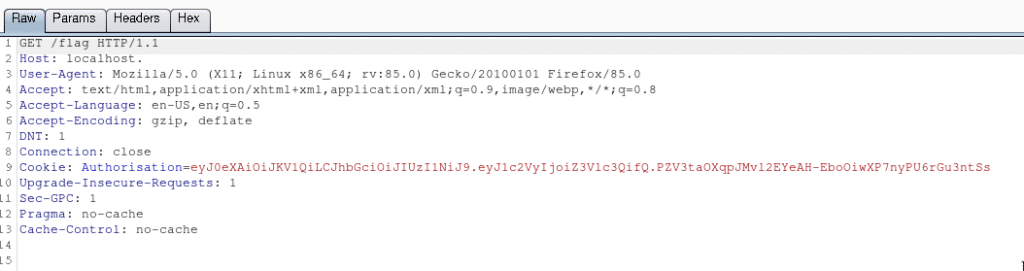
We can see there’s a cookie over here. And it looks like a JWT Token. Let’s head over to https://jwt.io/ and try to decode it.

Voila, it’s using a JWT Token to login to the application. We can try the key we saw in robots.txt here. As it’s using HS256, a symmetric cipher, the same key can be used to decode and encode the token.
Trying the key gives signature verified, that’s great. In the challenge description, it said that only the author has access to the REAL flag. Let’s try changing the user to the name of author, mystog3n.

Sending this as the cookie now gives logged in as mystog3n.

Checking the flag now gives another base64 encoded string.

Decoded it give us the flag: cohesion.ctf{JwT_t0k3N_t0_Th3_w1n}
3. Gamer Boy

Opening the link in the browser gives us the following page.

As we can see, there is a search box.

Maybe we can try SQL injection attack over here.
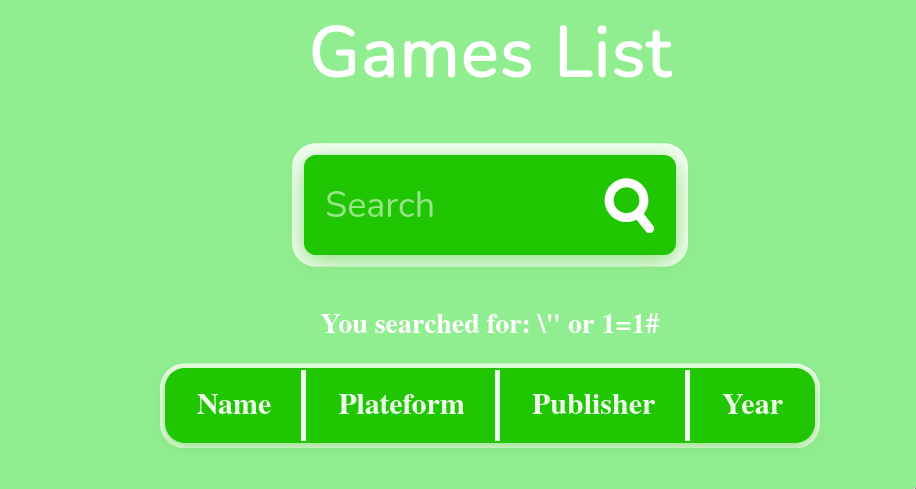
The double quotes (“) are escaped over here, so let’s try adding another backslash (\) to see that is it escaped.

No, it’s not! We’ve got SQL injection now. Let’s now try exploiting it.
Using the ORDER BY query, we know that there are 5 columns.

Now let’s try UNION SELECT.

Let’s get the table names from information scheme by using query:
\” union select 1,2,3,TABLE_NAME,5 from information_schema.tables;#


So there’s a table named “hidden“, this looks quite interesting. Let’s enumerate the columns in this tables with the query:
\” union select 1,2,3,COLUMN_NAME,TABLE_NAME from information_schema.columns;#


Aha, there’s a column named flag in the table hidden. Let’s get that by the query:
\” union select 1,2,3,flag,5 from hidden;#

Here’s the flag: cohesion.ctf{1nj3ct10n-4tt4ck_15-b35t}
4. Word in the Press

Opening up the website gives us this.

We can try to enumerate the users by adding a GET parameter ?author=1.

We can see that it redirects to https://ctf-word-in-the-press-t3ppmfifsq-as.a.run.app/author/mystog3n/, which means the username is mystog3n.

Let’s go the WordPress Login Page by heading to https://ctf-word-in-the-press-t3ppmfifsq-as.a.run.app/wp-login.php.

Fire up burp suit and intercept a login request.

Send this request to the intruder and set the attack to sniper mode with the password as the selected parameter.

Now add rockyou to the payload and start the attack.

After a while, you can see that butterfly has different content length than others so let’s try this as the password.

And we’ve got access to the WordPress Dashboard.

Head over to Appearance->Theme Editor.

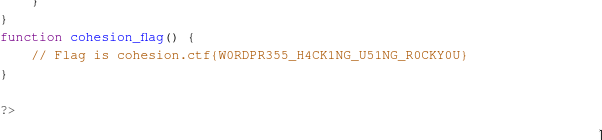
And now open up functions.php.

On scrolling down, we can see the flag cohesion.ctf{W0RDPR355_H4CK1NG_U51NG_R0CKY0U}
5. Jack Jill

Opening up the website gives us this.

We can find nothing over here. Let’s try gobuster on it.
It shows that there is a Readme.md and .git folder.
Opening Readme.md gives us this. Which is obviously a fake flag.

Let’s run git-dumper on it to get the git folder.
Now we have a local repository of the website. Running >git log says that this was the initial commit and nothings here now.


Running >git branch tells us that there are 2 branches in this repository, dev and final.

Let’s check the dev branch now. You can do so by running >git checkout dev

Now running >git log gives us the following commit history.

We can see that in the last commit flag was removed. So let’s see the changes since that commit by running
>git show 529926fecc442b805e516c451d34f5cc9e84f95c

Here’s the flag now: cohesion.ctf{git-c0mm1t1ng_t0_th3_c4u53}
Get the latest tech news and updates, ethical hacking tutorials, and cybersecurity tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.



Comments:
1 reply on “Web Challenges – Cohesion Writeup”
[…] Web Challenges […]