These are the writeups for Reverse Engineering Challenges of the Cohesion CTF by IEEE NCU.
1. Basic Rev

Downloading the file gives us an ELF binary.

Let’s make this executable and run this file.

It doesn’t seem like this will help. Let’s try running the strings command on it by typing >strings basic-rev

Voila, here’s the flag: IEENCU.CTF{R3V3R53_15_N0T_H4RD_0000}
2. Basic Rev 2

Again we get an ELF binary, let’s make it executable and try to run it.

We need to provide a flag as an argument and it’ll test that if it’s correct.
Let’s fire up Radare2 and view the assembly code to get the logic.
>r2 basic-rev2

We see that there is a main function, let’s disassemble it and see the source by typing in >pdf @main

It looks like it checks that each character is equal to certain values for the whole input string. Let’s go through the disassembled code and try to reverse the correct flag.
After some effort, we get that the flag is IEEENCU.CTF{B451C-R3V3R53-3NG-4-FUN}. Let’s try to enter this as the flag in the file and check if it’s correct or not.

And congratulation, this is the correct flag.
3. Andy

Once again we get a random file, let’s run file command on it to see what it is.

It’s a zip archive, let’s extract it and see what’s in it.


The extracted files looks like it’s from an android apk. Let’s use jadx to decompile this file.

Opening the extracted files and viewing the resources/AndroidManifest.xml file gives us the following.

This looks like a base64 encoded string, let’s decode it.

And here’s the flag: IEEENCU.CTF{W0W_4NDR01D_H45_4PK!!}
4. Pyro

Here, we’ve got an ELF executable. Let’s make it executable and run it.

And let’s run radare2 on it as well.

The functions doesn’t seem recognizable, probably because it’s stripped. On further investigation, we get to know that this file is made with python.
So on searching, we get to know that we can reverse it by using pyinstxtractor by extremecoders-re. Using this we can reverse the file by the commands
>objcopy –dump-section pydata=pyro.dump pyro
>python pyinstxtractor.py pyro.dump

In the extracted folder, there is a file py-ro.pyc. Let’s try running strings command on it.

And here’s the flag: IEEENCU.CTF{TH3_FUN_0F_R3VERS1NG-PYTH0N}
5. Grep the Flag

Again, an ELF file. Repeat the steps to make it executable now.

It seems like the grep command on Linux. Let’s try >grep help

It surely is the grep command. Now let’s try the string command and grep the flag format on it.

We can see there is an option to test if the flag is correct or not. Let’s open this up in radare2.

We can see it has a lot of functions. Anyways, let’s try decompiling @main

Upon going through the function, we can see that a function sym.val_f is called and then according to the output, string “Correct Flag!” is printed.

Let’s now analyse this function sym.val_f. This looks a bit complicated but don’t worry, you’ll understand it with practice.
Here it seems like each character in the flag is XORed with something.

And then 2 is added to each character.

Which is then base64 encoded.

And finally compared against a string to check if it’s correct or not in parts.

Upon analyzing, we find that the base64 string is: e3V1eXwnY0e3V1eXwnY0ZjMEfndoaCsDbnWBBXY/BA9hSjZURmE2SH8= and the string it was XORed was: 06624f4da489e774a32292a235373b38.
Now we have all the things we need. We have to first base64decode the string, followed by subtracting 2 from each of the character. And at last XOR it with the other string.
We can do this with the following program:

Compiling and running it will give us the following output:

Here’s the flag: IEEENCU.CTF{GR3PP1NG_TH3_FL4G_15_H4RD_4F}
6. Not So Basic

Repeat the first steps for this ELF executable again and run it.

It is again checking the flag against the input. Open up Radare2 and analyze it.

Decompiling the @main gives us following.

Over here, it looks like some calculations are done on the tax register, and then the value stored in it is treated as a function and called.
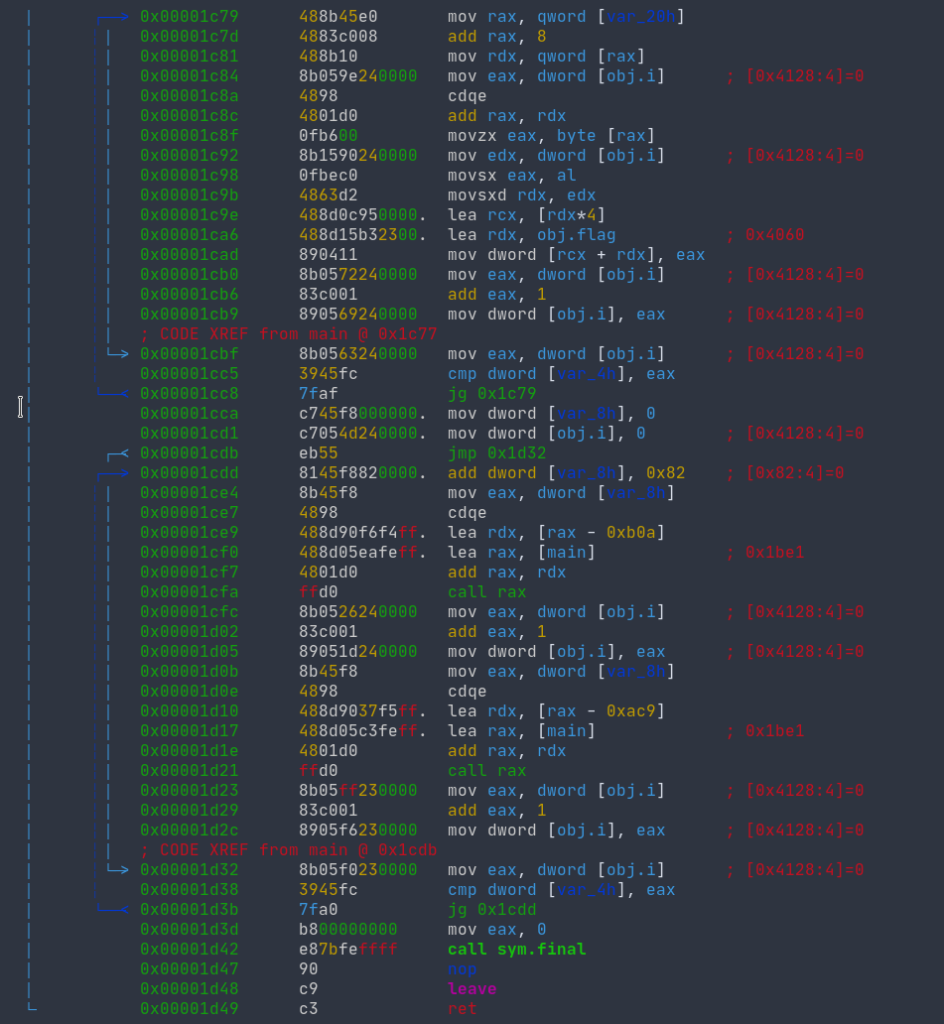
And this all is in a loop. Analyzing it a bit further, it seems as if all these functions are being called by their addresses instead of their names.

Let’s try to see one such function call.

Here, it is comparing values of flag and if it’s correct, it continues or else it exits.
And each of the function call compares the value of one character.

And at the end, we have this sym.final function.

Going through the addresses and checking each of the function for characters of the flag gives us the flag: IEEENCU.CTF{FUNCT10N5-4R3NT-FUN-4ND-345Y}
Get the latest tech news and updates, ethical hacking tutorials, and cybersecurity tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.



Comments: